The hidden weaknesses of multifactor authentication
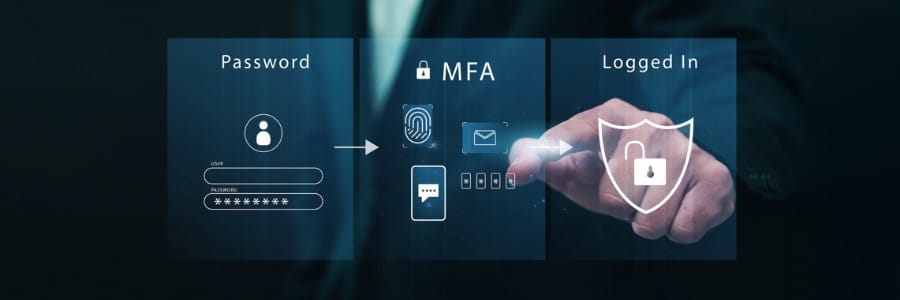
Multifactor authentication (MFA) works by requiring users to provide more than one form of identification when logging into a system or account. This extra layer

Multifactor authentication (MFA) works by requiring users to provide more than one form of identification when logging into a system or account. This extra layer

Upgrading your company’s servers is a crucial decision that affects everything from operations to long-term growth. Rather than rushing into a replacement, it’s important to

With remote and hybrid work now the norm, visual collaboration tools have become essential for allowing teams to brainstorm, plan, and innovate together in real

Imagine a customer walking into your physical store, looking around for five seconds, and then immediately walking out without saying a word. The same thing

Cyberattacks, technical failures, or simple human error can creep up out of nowhere. And when they occur, businesses are often left scrambling to recover lost

Cybersecurity experts Rob Wright (Dark Reading), David Jones (Cybersecurity Dive), and Alissa Irei (TechTarget Search Security) recently came together to discuss the future of online

Mercenary spyware is targeting iPhones again, and Apple’s latest security patch helps users only on iOS 26. With millions slow to update, security experts warn

Microsoft’s upcoming Windows 11 26H1 update is rolling out only to devices powered by Snapdragon chips, at least for now. While it might seem like

Cloud computing is the use of remote servers to store, manage, and process data, freeing businesses from the limits of physical infrastructure. For small businesses,

Your bathroom, your kitchen table, even your dreams — if it’s part of your life, health tech wants in. CES 2026, the world’s biggest technology

* The referral must sign up for IT managed services in order for the referrer to receive the reward.